-
Creator 版本:3.7.3
-
目标平台: Android
-
重现方式:随便写个effect,使用cc_time刷新渲染,如
vec4 fragColor = vec4(0.5sin(6.283(v_uv0.x - v_time.x + vec3(0, -0.33333, 0.33333)))+0.5, o.a);
o *= fragColor;
return CCFragOutput(o); -
首个报错:13
 19.601 12321-12503 libc com…bet.okeysohbet A Fatal signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0 in tid 12503 (RenderThread), pid 12321 (okeysohbet:game)
19.601 12321-12503 libc com…bet.okeysohbet A Fatal signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0 in tid 12503 (RenderThread), pid 12321 (okeysohbet:game)
13 19.926 12554-12554 DEBUG pid-12554 A *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
19.926 12554-12554 DEBUG pid-12554 A *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
13 19.926 12554-12554 DEBUG pid-12554 A Build fingerprint: ‘Redmi/dandelion/dandelion:11/RP1A.200720.011/V12.5.18.0.RCDCNXM:user/release-keys’
19.926 12554-12554 DEBUG pid-12554 A Build fingerprint: ‘Redmi/dandelion/dandelion:11/RP1A.200720.011/V12.5.18.0.RCDCNXM:user/release-keys’
13 19.927 12554-12554 DEBUG pid-12554 A Revision: ‘0’
19.927 12554-12554 DEBUG pid-12554 A Revision: ‘0’
13 19.927 12554-12554 DEBUG pid-12554 A ABI: ‘arm’
19.927 12554-12554 DEBUG pid-12554 A ABI: ‘arm’
13 19.929 12554-12554 DEBUG pid-12554 A Timestamp: 2023-09-06 13
19.929 12554-12554 DEBUG pid-12554 A Timestamp: 2023-09-06 13 19+0800
19+0800
13 19.929 12554-12554 DEBUG pid-12554 A pid: 12321, tid: 12503, name: RenderThread >>> com.okeysohbet.okeysohbet:game <<<
19.929 12554-12554 DEBUG pid-12554 A pid: 12321, tid: 12503, name: RenderThread >>> com.okeysohbet.okeysohbet:game <<<
13 19.929 12554-12554 DEBUG pid-12554 A uid: 10239
19.929 12554-12554 DEBUG pid-12554 A uid: 10239
13 19.929 12554-12554 DEBUG pid-12554 A signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0
19.929 12554-12554 DEBUG pid-12554 A signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x0
13 19.930 12554-12554 DEBUG pid-12554 A Cause: null pointer dereference
19.930 12554-12554 DEBUG pid-12554 A Cause: null pointer dereference
13 19.930 12554-12554 DEBUG pid-12554 A r0 00068646 r1 00000000 r2 00000000 r3 00000000
19.930 12554-12554 DEBUG pid-12554 A r0 00068646 r1 00000000 r2 00000000 r3 00000000
13 19.930 12554-12554 DEBUG pid-12554 A r4 af686008 r5 af68602c r6 00000000 r7 00000000
19.930 12554-12554 DEBUG pid-12554 A r4 af686008 r5 af68602c r6 00000000 r7 00000000
13 19.930 12554-12554 DEBUG pid-12554 A r8 eabe12b4 r9 00000000 r10 00000000 r11 00000001
19.930 12554-12554 DEBUG pid-12554 A r8 eabe12b4 r9 00000000 r10 00000000 r11 00000001
13 19.930 12554-12554 DEBUG pid-12554 A ip eabdce88 sp aee6ea30 lr eab5a0e5 pc eab74600
19.930 12554-12554 DEBUG pid-12554 A ip eabdce88 sp aee6ea30 lr eab5a0e5 pc eab74600
13 19.946 12554-12554 DEBUG pid-12554 A backtrace:
19.946 12554-12554 DEBUG pid-12554 A backtrace:
13 19.947 12554-12554 DEBUG pid-12554 A #00 pc 0004e600 /apex/com.android.runtime/lib/bionic/libc.so (je_large_dalloc+32) (BuildId: e44bedae375b44720c6f409b54f509f4)
19.947 12554-12554 DEBUG pid-12554 A #00 pc 0004e600 /apex/com.android.runtime/lib/bionic/libc.so (je_large_dalloc+32) (BuildId: e44bedae375b44720c6f409b54f509f4)
13 19.947 12554-12554 DEBUG pid-12554 A #01 pc 000340e1 /apex/com.android.runtime/lib/bionic/libc.so (je_free+1580) (BuildId: e44bedae375b44720c6f409b54f509f4)
19.947 12554-12554 DEBUG pid-12554 A #01 pc 000340e1 /apex/com.android.runtime/lib/bionic/libc.so (je_free+1580) (BuildId: e44bedae375b44720c6f409b54f509f4)
13 19.948 12554-12554 DEBUG pid-12554 A #02 pc 000c8df5 /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
19.948 12554-12554 DEBUG pid-12554 A #02 pc 000c8df5 /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
13 19.948 12554-12554 DEBUG pid-12554 A #03 pc 000cc8a7 /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
19.948 12554-12554 DEBUG pid-12554 A #03 pc 000cc8a7 /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
13 19.948 12554-12554 DEBUG pid-12554 A #04 pc 000ccbcd /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
19.948 12554-12554 DEBUG pid-12554 A #04 pc 000ccbcd /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
13 19.948 12554-12554 DEBUG pid-12554 A #05 pc 000d1c57 /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
19.948 12554-12554 DEBUG pid-12554 A #05 pc 000d1c57 /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
13 19.948 12554-12554 DEBUG pid-12554 A #06 pc 0005371f /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
19.948 12554-12554 DEBUG pid-12554 A #06 pc 0005371f /vendor/lib/egl/libGLESv2_mtk.so (BuildId: 72cc0c34626bcbd2841c34a3f530fd65)
13 19.949 12554-12554 DEBUG pid-12554 A #07 pc 0002b7d7 /vendor/lib/libsrv_um.so (BuildId: 889b1247792688ac7abc78a80e0a010b)
19.949 12554-12554 DEBUG pid-12554 A #07 pc 0002b7d7 /vendor/lib/libsrv_um.so (BuildId: 889b1247792688ac7abc78a80e0a010b)
13 19.949 12554-12554 DEBUG pid-12554 A #08 pc 000aaf93 /apex/com.android.runtime/lib/bionic/libc.so (__pthread_start(void*)+40) (BuildId: e44bedae375b44720c6f409b54f509f4)
19.949 12554-12554 DEBUG pid-12554 A #08 pc 000aaf93 /apex/com.android.runtime/lib/bionic/libc.so (__pthread_start(void*)+40) (BuildId: e44bedae375b44720c6f409b54f509f4)
13 19.949 12554-12554 DEBUG pid-12554 A #09 pc 00064203 /apex/com.android.runtime/lib/bionic/libc.so (__start_thread+30) (BuildId: e44bedae375b44720c6f409b54f509f4)
19.949 12554-12554 DEBUG pid-12554 A #09 pc 00064203 /apex/com.android.runtime/lib/bionic/libc.so (__start_thread+30) (BuildId: e44bedae375b44720c6f409b54f509f4) -
重现概率: mtk芯片100%
起因是游戏某个版本更新后,陆续有玩家反馈进不去游戏,一进就闪退,但是我们自己的测试机复现不出来,最初怀疑是代码逻辑问题,但是通过崩溃玩家的逻辑日志查不到任何问题,后来通过崩溃堆栈看到了libGLESv2_mtk.so的相关信息,又怀疑是引擎底层渲染逻辑的问题,带着这个怀疑google了一下,发现unity甚至是android原生开发也有人遇到了同样的问题。幸好同事想起来mtk这个关键词,于是去看了崩溃玩家的手机芯片是果然都是mtk的,于是找到一台mtk芯片的测试机果然复现了,通过排除法最后找到导致崩溃的原因就是某个effect使用了cc_time去动态更新,虽然定位到问题,但是没有解决办法,所以想问问论坛里的大神们。我目前是暂时去掉了cc_time相关的逻辑。

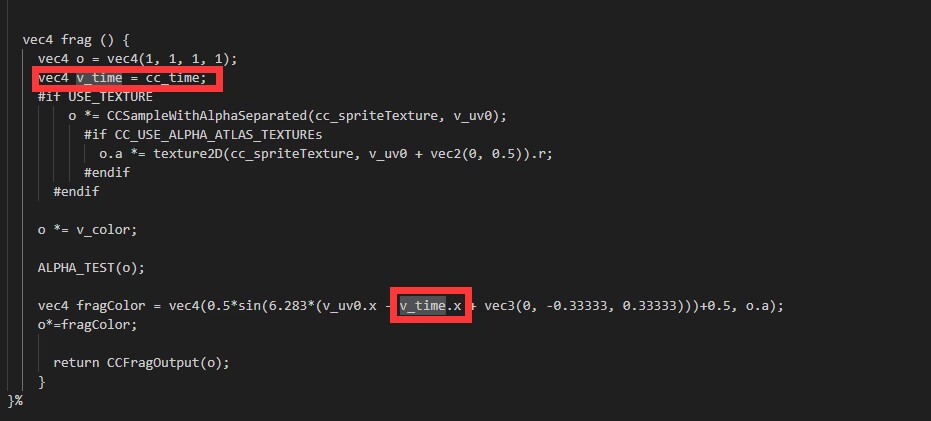 直接写在片元着色器里,不要通过顶点着色器中转试试
直接写在片元着色器里,不要通过顶点着色器中转试试